Public Key Encryption¶
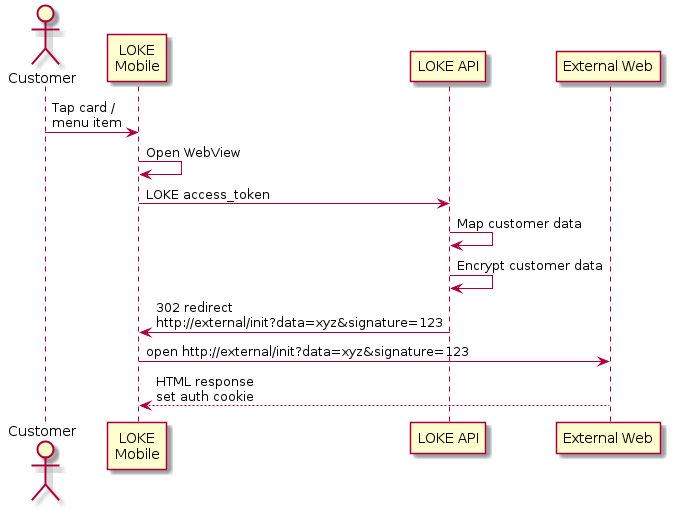
LOKE allows for SSO by passing data using RSA public key encryption. This works by LOKE's back-end generated a JSON model of the customer, encrypting it using a public key provided by you, and redirecting to your server with the encrypted data attached as a query string parameter.
Your server may now decrypt the data with the private key you will have created, and deserialise the JSON object.
Tip
There is lots of info on generating RSA private/public key pairs online. This can be done in code, or using tools such as OpenSSL, eg: https://rietta.com/blog/2012/01/27/openssl-generating-rsa-key-from-command/
Warning
Secure your private key. Anyone who has access to it will be able to decrypt the sensitive customer information.
Custom JSON models for the user can be created, but will always contain:
expiry- we will always pass a ISO1601 timestamp, typically for 60 seconds in the future, so you know when it is unsafe to use the encrypted data.ssoId- a UUID/GUID generated with each packet, so you can ensure the same request is not used twice.
Note
It is strongly recommended to obey the expiry field.
The following query string parameters will be sent with the GET request to your server:
- data - contains the encrypted data.
- signature - we will always sign the data so you can ensure it comes from us.
Warning
You should always check the signature field. You shouldn't trust your public key is secure - it's called public for a reason. Anyone with the public key can send you valid encrypted data. You shouldn't log someone in to your system without ensuring the request comes from a verified source.
Tip
To validate the signature you must request the public key from LOKE support.
Note
Note any session identification and/or token must be provided in the URL. Headers and cookies are not supported. If cookie authentication is required then another intermediate step is required (where the third-party server reads the session ID and sets a cookie in the response).